Developer Resources
Internet Identity Code Verification
Step-by-step guide of verifying that the authentication system works correctly. Let’s verify the Internet Identity’s code.

Confirming the Internet Identity Authentication System
Step-by-step guide of verifying that the authentication system works correctly
In the following guide, we will take a look at how you can confirm that the blockchain authentication system of the Internet Identify is running the correct code.
Verifying the Internet Identity Code
The Internet Identity is used on the Internet Computer as a cryptographic authentication system that allows users to seamlessly log into various dApps, including the NNS front-end dApp. To confirm the service is handling their credentials securely and confidentially, users can directly confirm that they are not being tracked by the Internet Identity.
Here are the steps to verify the Internet Identity is running the precise code it is supposed to run.
Identifying the Code that is Running
It is not possible to download the Wasm code of a canister smart contract as developers may wish to keep the code of their services private to protect their intellectual property. However, the Internet Computer exposes the Wasm module’s hash. With the help of dfx, you can access this hash:
Let’s have a look at each part of the hash in more detail:
You can use the canister ID of the governance canister as “controller.” The result shows you that the Network Nervous System (NNS) controls the Internet Identity and that changes to its code need to be voted on via governance proposals. Consequently, the code of the Internet Identity cannot be changed if there is no proposal or if a proposal has been rejected.
The SHA-256 hash is the “module hash” of the deployed .wasm whose trace we are going to follow next.
Identifying the Correct Commit
The Internet Identity can be upgraded through proposals to the NNS that approved by governance votes. For this reason, we can search the NNS proposals repository to find such a proposal. The proposals repository is located in the proposals/network_canister_management directory
In the next step, search for the latest approved proposal that was used to upgrade the Internet Identity. In our case, the folder includes many proposals for different canisters. Additionally, the file name may complicate your search. The best approach is to navigate to the bottom of the list and start from there. Focus on the second column where you can see the last commit’s title when a file was created or modified.
In our case, we are interested in the second to last one.
In the file, rationales are listed and we can find an overview of the changes. We can also see from the file that bd51eab is the commit the Internet Identity was upgraded to. Another piece of information we can see from the file is the wasm hash (d4a...c04) which is the same as we’ve seen above.
Identifying the Source
Once we have identified the revision, we can search for the source to check out the revision bd51eab:
If you take a closer look at the last line, the revision was tagged with a tag name that included the proposal description file name.
Reproducing the Build
If you have a look at the README.md file, you will see that it includes the following build instructions:
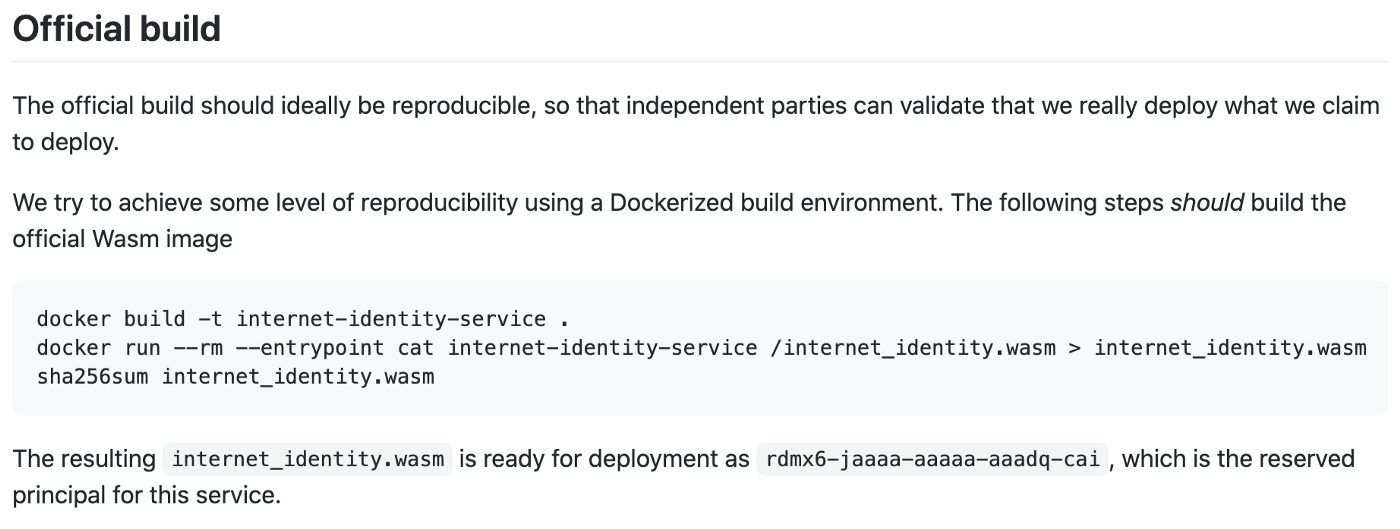
It’s enough to run the first command which prints the hash. It’s not necessary to copy the .wasm file from the Docker canister.
If it says that it has successfully run the built and tagged the latest upgrade, we know that the hashes match.
Verifying the Canister ID
Running our previous commands returns the module for the canister rdmx6-jaaaa-aaaaa-aaadq-cai. The Internet Identity, however, is a web application located at identity.ic0.app
This is because the mapping is hard-coded until a DNS-like hostname registry is implemented for storing a mapping from names to canister IDs.
Relevant for our purposes is the “Certifying Service Worker” which a browser downloads whenever any *.ic0.app URL is accessed. The code of the service worker intercepts requests to the domain, maps these requests to a query call, and then makes use of certified variables so that it can validate the response. We can find the mapping in the code here: https://github.com/dfinity/agent-js/blob/6e8c64cf07c7722aafbf52351eb0f19fcb954ff0/apps/sw-cert/src/sw/http_request.ts#L12


