Developer Resources
Achieving Consensus
Find out how consensus is achieved on the Internet Computer and how long the asynchronous finalization of the consensus protocol takes

Consensus Protocol
Learn more about the Internet Computer’s Consensus Protocol
Asynchronous Finalization of the IC Blockchain
Reliability and security are the two key features of the Internet Computer blockchain. The network is powered by node machines hosted in data centers all across the world. The Internet Computer Protocol (ICP) is used by the nodes for communication. In doing so, a virtual Internet Computer is formed which allows developers to develop and deploy canister smart contracts in a reliable and secure manner.
The aforementioned properties of reliability and security are accomplished by utilizing a novel consensus protocol.
Additionally, the Internet Computer is designed to scale indefinitely, allowing an unlimited number of decentralized applications to run on the platform. The network’s secure scalability is accomplished by utilizing the Internet Computer’s peer-to-peer layer.
The Internet Computer can seamlessly grow its capacity by adding new subnets and by splitting existing ones. Furthermore, Chain Key Cryptography enables secure communication between canisters hosted on different subnets.
The Importance of Consensus
A consensus protocol is required to utilize replication for increasing the network’s security. This allows the correct state of a subnet to remain unaffected should replicas become malicious or unavailable – as long as the majority of node machines continue to function correctly.
These are the requirements for a subnet:
Subnets need to be able to process different messages (sent from users to canisters and canisters to other canisters)
- Messages need to be processed in the same order to ensure that replicas end up in the same state
The problem lies therein that each replica in a subnet may see all the messages in a different order.
Consensus properties
The consensus protocol places messages in blocks. Agreement is reached using a blockchain.
For the purpose of this example, we assume there are n replicas running a subnet together
We want this even if up to f of the n nodes misbehave, with n = 3f+1. In the example above, we use n = 4, f = 1.
To reach consensus, a blockchain is used. Messages that need to be processed by a subnet are grouped and then placed in blocks. Each block is pointing to a previous block, forming a connected chain of blocks. If all replicas agree on the state of the blockchain, security is achieved as this provides a message ordering.
The Four Main Parts of the Consensus Protocol
The design of the consensus protocol is tailored to the specific needs of the Internet Computer network. Let’s have a look at its main parts:
Block making
A replica within the subnet serves as block maker. It proposes a new block which extends the existing chain. The replicon gathers incoming messages and groups them into a block. The block is it then sent to the subnet’s other replicas with a proposal to extend the blockchain with it.
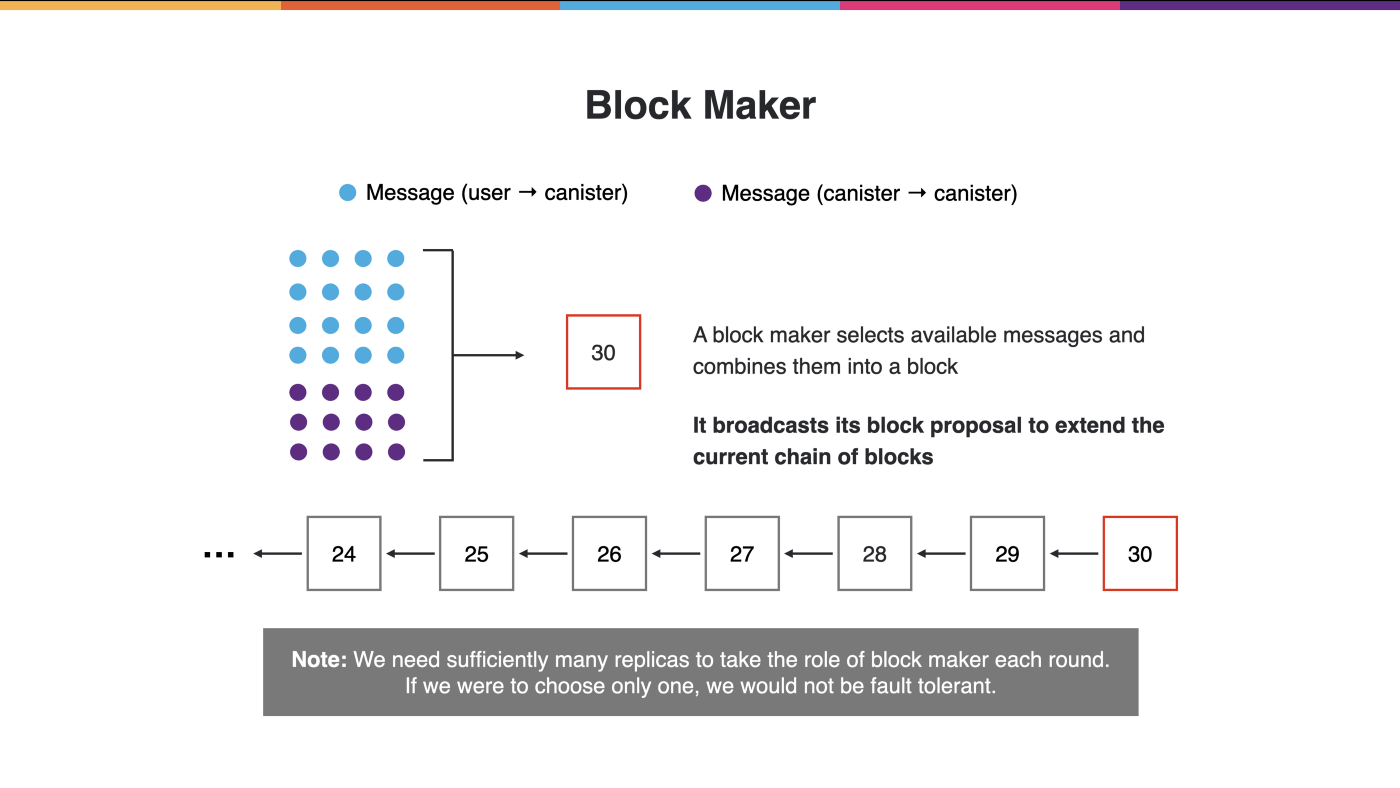
Many replicas is within the subnet can serve as block makers to ensure that the consensus protocol continues to work even if nodes are misbehaving. For this reason, it is not possible to elect one single block maker.
Notarization
Block proposals may be invalid because there is not a single block maker. Notarization ensures that there is at least one valid block to extend the blockchain.
To ensure the liveness property is adhered to, the notary can sign both blocks so that at least one of the blocks becomes notarized.
Random beacon
Agreement has not yet been reached as multiple blocks may have been notarized at every height. The number of notarized blocks is therefore reduced by adding the random beacon to the protocol. It is an unpredictable value that is added at every height as a random-looking artifact.
Finalization
To observe agreement a separate asynchronous finalization process is used. It lets the replicas know that they can accept the chain. With the Internet Computer’s finalization approach, blocks can be finalized in less than two seconds.